Security Vulnerabilities
This section is dedicated to material related to security vulnerabilties, for the awareness and development of secure practises.
Vulnerabilty Databases
- Mitre ATT&CK - ATT&CK is a database of knowledge related to the security of enterprises, mobiles and industrial contol systems. It includes knowledge on adversary's tactical goals, techniques, and ways to mitigate them.
- Mitre Common Weakness Enumeration (CWE) - CWE is a community-developed database of security vulnerabilities, trusted by security foundations such as OWASP.
Reflection
I really appreciate the work that goes into these databases, particularly the ontological part of the design. Identifying the attributes and relationships that exists between concepts, that subsume all current knowledge while making it accessible, is fascinating. I find the fact that the above databases are valuable to the security community, encouraging too, as I try to find the balance between motives of aesthetics and practicality. I would like to contribute to an ontological project, and I've now seen how that interest intersects with security to become communally useful. Essentially an ontology is a formal hub of knowledge that's made accessible using a well-defined structure. The security-centred databases linked above, share details worth accomodating as a software engineer, for the improvement of software quality and therefore service. As a software engineer myself, I could learn more from these databases to make my software more secure.
Glossary
Insider Risk
"The potential for damage to be done maliciously or inadvertently by a legitimate user with privilleged access to systems, networks or data." ( NCSC )
Software Vulnerability
"A security flaw, glitch, or weakness found in software code that could be exploited by an attacker." ( NIST )
Example
Below is an example of a software vulnerability that I found during a group project, in which we were tasked with creating secure CRUD software.
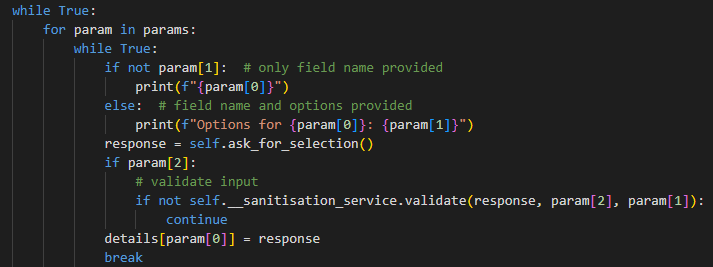
The programme involved the loop above, which parses a request, and depending on the details of the request; it gets input from a user and then validates that the input is an acceptible format. The vulnerability comes from optional information being missing in the request as below:
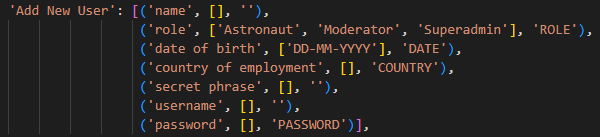
Some of the params in the request, such as 'name', include an empty string as the third element. This means that any input the user provides for a name will not be validated in the loop. This is a vulnerability because any input the user provides is later inserted into a database, and therefore might be exploited by an attacker, through an SQL injection for example.
To view the rest of the project codebase, click here.
Tips for Resilience to Attacks
This was my submission to a blogging activity, in which we were tasked to talk about How to overcome insider cyber security threats:
"A study by Zimmerman and Renaud (2019) found that people are often seen by government, industry and hackers as security threats. Justification for that view stems from observations such as:
- People don't always follow best security practices.
- People unknowingly create software vulnerabilities.
- People can be malicious.
So, how can we overcome cybersecurity threats from the inside?
Follow the Best Security Practices
It's important to establish what the best security practices actually are. Risk communication and consultation is a continual and iterative process to provide, share and obtain information (ISO, 2018). Promote a culture of learning and sharing of expertise to ensure everybody is aware of the best practises. Cybersecurity is dynamic, so requires active learning to keep up. Being a part of an information sharing community is beneficial for that reason too (Skopik et al, 2016).
Reduce Software Vulnerabilities
Reducing software vulnerabilities is much easier said than done. A balance of resilience against attacks is just as vital as resistance to them (Zimmerman and Renaud, 2019). Software metrics such as the common vulnerability scoring system (CVSS) attempt to measure security vulnerabilities with regards to impact and likelihood of threats (Fenton & Bieman, 2015), providing some control as to where to build resistance and resilience into your system. But, security metrics such as CVSS do not identify specific software vulnerabilities, because those vulnerabilities stem from code reliability. Software reliability models assume that systems will eventually fail (Fenton & Bieman, 2015). The critical systems of the international space station for example are built with two-failure tolerance, so that if something goes wrong, it's less likely to result in a catastrophic event (NASA, 2007). Boost resistance and resilience.
Don't be Malicious
Roberts et al (2018) found that no security solution can totally mitigate the threat of malicious betrayal. Malice is a societal concern, and the law is its deterrent. Facilitating the development of genuinely rewarding incentives on an individual level; to complement the possibility of punishment for wrong doing gives your team more incentive to protect itself. This positive organisational psychology, combined with security resilience, and culture of learning, I believe, will help you overcome insider cyber security threats.
References
- Fenton, N. & Bieman, J. (2015) Software metrics: a rigorous and practical approach. 3rd ed. Boca Raton, Florida, USA: CRC Press. 466-477.
- ISO. (2018) ISO/IEC 27000:2018 (en) Information technology - Security techniques - Information security management systems - Overview and Vocabulary. Available from: https://www.iso.org/obp/ui/#iso:std:iso-iec:27000:ed-5:v1:en:sec:3 [Accessed 12 May 2023].
- NASA. (2007) Final Report of the International Space Station Independent Safety Task Force. Available from: https://www.nasa.gov/pdf/170368main_IIST_%20Final%20Report.pdf [Accessed 13 May 2023].
- Roberts, S., Hammoudeh, M. & Dehghantanha, A. (2018) A Systematic Review of the Availability and Efficacy of Countermeasures to Internal Threats in Healthcare Critical Infrastructure. IEEE Access. 6. 25167-25177. Available from: https://doi.org/10.1109/ACCESS.2018.2817560 [Accessed 13 May 2023].
- Skopik, F, Settanni, G. & Fiedler, R. (2016) A problem shared is a problem halved: A survey on the dimensions of collective cyber defense through security information sharing. Computers & Security. 60. 154-176. Available from: https://doi.org/10.1016/j.cose.2016.04.003 [Accessed 13 May 2023].
- Zimmerman, V. & Renaud, K. (2019) Moving from a 'human-as-problem' to a 'human-as-solution' mindset. Journal of Human-Computer Studies.131. 169-187. Available from: https://doi.org/10.1016/j.ijhcs.2019.05.005 [Accessed 13 May 2023].
Bilbliography
- MITRE. (2023) Phishing. Available from: https://attack.mitre.org/techniques/T1566/ [Accessed 13 May 2023].
Vulnerability Severity Score
This was my submission to a task in which we were asked to design an ontology for recording vulnerabilities, a severity score, and impact.
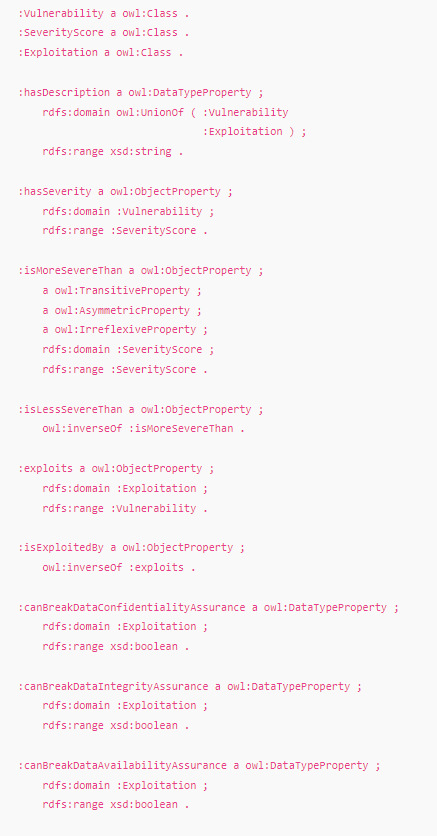
The ontology is written in OWL, and includes three entities: Vulnerability, SeverityScore and Exploitation.
Bibliography
- W3C. (2012) OWL 2 Web Ontology Language. Structural Specification and Functional-Style Syntax (Second Edition). Available from: https://www.w3.org/TR/owl2-syntax/ [Accessed 24 June 2023].
- W3C. (2023) OWL 2 RDF 1.2 Schema. Available from: https://www.w3.org/TR/rdf12-schema/ [Accessed 24 June 2023].
- W3C. (2023) W3C XML Schema Definition Language (XSD) 1.1 Part 2: Datatypes. Available from: https://www.w3.org/TR/xmlschema11-2 [Accessed 24 June 2023].